Trezor Login: A Comprehensive Guide to Secure Cryptocurrency Access
In the dynamic world of cryptocurrencies, security is not just a necessity—it’s a priority. With the rise in digital asset adoption, safeguarding crypto holdings through reliable hardware wallets has become a critical step for investors. Among the top-tier solutions in the market, Trezor stands out as a trusted name, offering unparalleled security features combined with user-friendly interfaces. One of the most essential aspects of using Trezor is the Trezor login process, which allows users to safely access their wallets and manage digital assets without compromising privacy or control. This article provides an in-depth exploration of the Trezor login system, its features, functionality, and importance in today’s digital finance ecosystem.
Understanding Trezor: The Foundation of Secure Crypto Storage
Trezor is a hardware wallet developed by SatoshiLabs, designed to protect cryptocurrencies from online threats such as hacking, phishing, and malware attacks. Unlike software wallets or exchanges, which store private keys online, Trezor securely keeps your keys offline within the device. This "cold storage" approach ensures that even if your computer is compromised, your funds remain safe.
Trezor wallets are compatible with thousands of cryptocurrencies including Bitcoin, Ethereum, Litecoin, and ERC-20 tokens. The wallet comes in two primary models—Trezor Model One and Trezor Model T—both designed with strong cryptographic architecture, PIN protection, and recovery seed systems.
The Role of Trezor Login: More Than Just Access
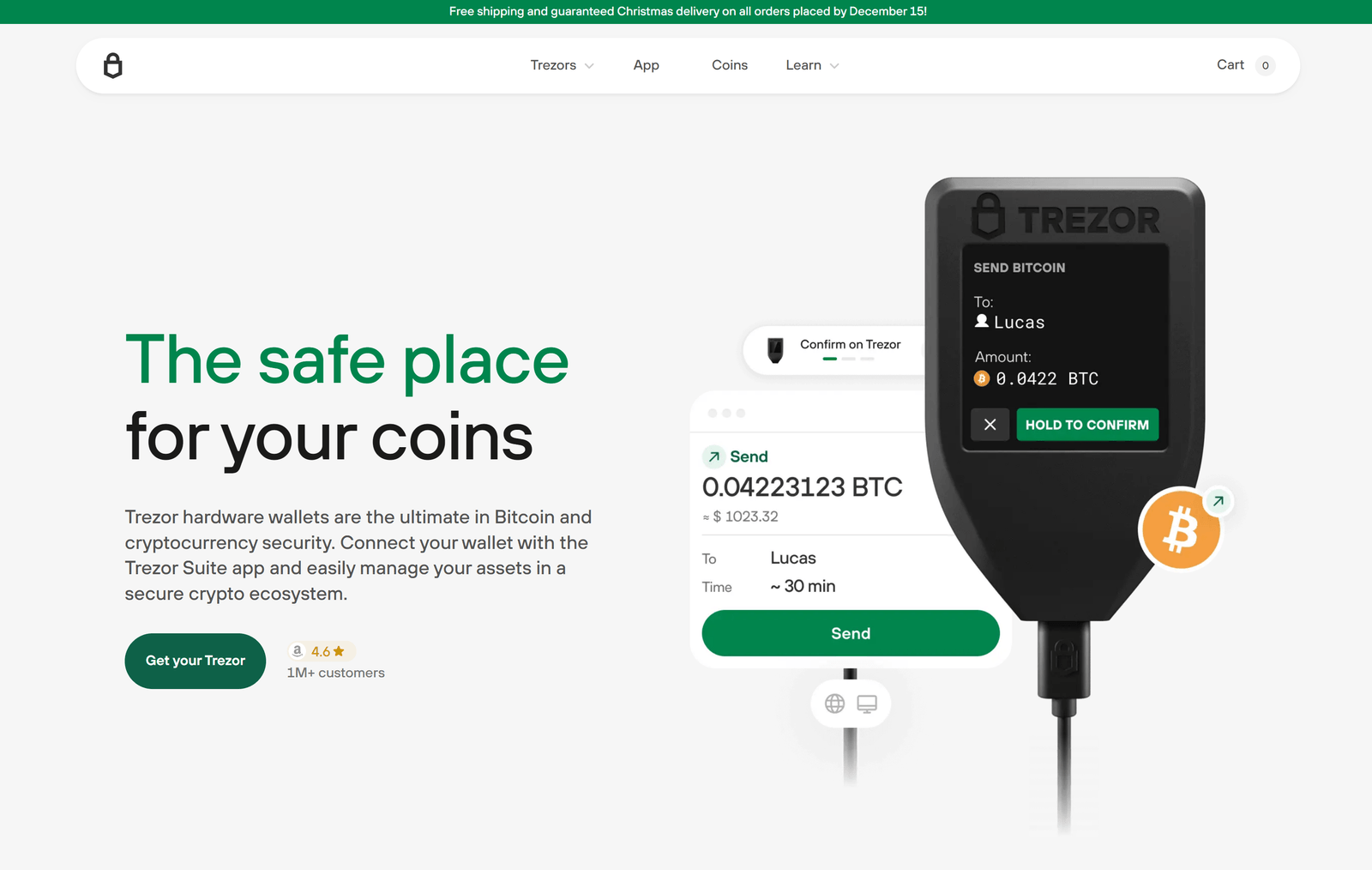
The Trezor login is not a conventional login with a username and password. Instead, it is a multi-layered authentication process that involves direct hardware interaction, making unauthorized access virtually impossible.
Here’s why the Trezor login process is more secure than traditional logins:
- No Credentials Stored Online: Unlike centralized platforms, there’s no stored login data that can be hacked.
- Hardware-Based Authentication: All sensitive operations require physical confirmation on your Trezor device.
- Decentralized Key Management: The private keys never leave the device and are never exposed online.
How to Perform a Trezor Login: Step-by-Step Process
Logging into your Trezor wallet is a straightforward process that prioritizes both security and ease of use. Follow these steps for a successful login:
- Connect Your Trezor Device Begin by plugging your Trezor wallet into your computer or mobile device using a USB cable.
- Open Trezor Suite or Browser Interface Navigate to the Trezor Suite application or open the Trezor web interface. Both platforms allow you to interact with your wallet securely.
- Verify Device Connection Once connected, the Suite or browser will automatically detect your Trezor device. You will be prompted to confirm the connection on your hardware wallet.
- Enter Your PIN You’ll be asked to enter your secure PIN using a randomized keypad layout shown on your computer screen, which you then replicate on the Trezor device. This protects against keylogging attacks.
- Access Your Wallet Dashboard After successful authentication, you’ll gain access to your wallet interface, where you can view balances, send and receive crypto, and manage accounts.
Advanced Features Supporting Secure Login
Trezor enhances the login experience with advanced security tools that make it a fortress for your digital wealth:
- Passphrase Support: An optional but powerful feature, the passphrase adds an additional layer of encryption, essentially creating a “wallet within a wallet.”
- Shamir Backup: This feature lets users split the recovery seed into multiple parts, ensuring no single point of failure in case of device loss.
- Biometric-Free Security: Trezor intentionally avoids biometric systems, which can be bypassed, and instead focuses on cryptographic strength.
Trezor Login on Third-Party Platforms
Besides using Trezor Suite, users can also log in to third-party services and decentralized applications (dApps) via Trezor. Platforms like MyEtherWallet, MetaMask, and various DeFi interfaces offer Trezor integration.
To access these, simply choose “Login with Trezor” on the third-party site, connect your device, and confirm access on the hardware wallet. This enables you to interact with Ethereum-based tokens and DeFi services securely, using your Trezor as the authentication gateway.
Troubleshooting Trezor Login Issues
In rare cases, users might encounter difficulties during the login process. Here are some quick troubleshooting tips:
- Update Firmware: Ensure your Trezor device is running the latest firmware.
- Use Original Cables: Unofficial or faulty USB cables can disrupt connection.
- Browser Compatibility: Use supported browsers like Chrome or Firefox for optimal performance.
- Clear Cache or Try Trezor Suite App: If login fails on the browser, use the Trezor Suite desktop app for a more stable experience.
Final Thoughts: Why Trezor Login is a Benchmark for Security
The Trezor login system exemplifies the future of secure authentication in the crypto space. Unlike traditional systems that are vulnerable to breaches, Trezor’s hardware-based security model gives users full control over their assets without ever exposing private keys to the internet. Its unique combination of offline key storage, PIN protection, passphrase integration, and seamless interface makes it one of the most secure and user-centric login systems available.
Made in Typedream